Today we are telling you in this article about the top 5 security features of Office 365 Advanced Threat Security. In this article, we will tell you a lot of details so that you can think about using it and why you should use Office 365 ATP in your organization. Interested in implementing Office 365 sophisticated threats security?
What is Office 365 Advanced Threat Security?
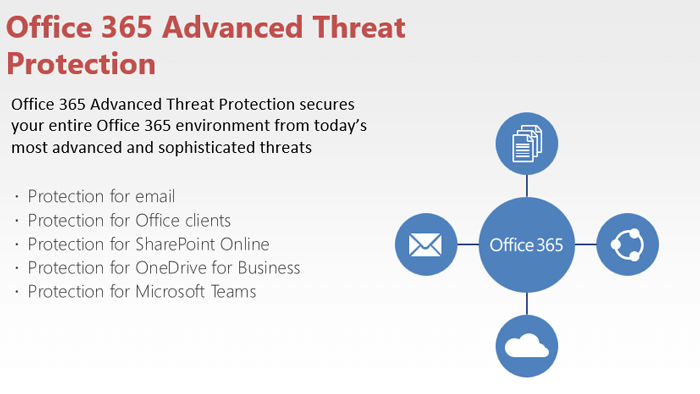
Office 365 Advanced Threat Protection You can ensure that you are not the victim of a number of new malware campaigns that are beginning every day. Securing your organization with things like email, online storage solutions, Office 365 ATP Essentials Online Protection Exchange Security features to provide zero-day better protection for your organization, secure your attachment, and not malicious links in real-time is.
Office 365 Advanced Threat Security including Enterprise E3 and E5 in your Office 365 license. It can be added at a reduced monthly fee of only 2.40 CAD/user in addition to multiple exchange plans and Office 365 subscriptions. Not a bad investment, given that it is done to prevent potential violations, saving you thousands of dollars! But if the fee is not enough to encourage you to enter your security infrastructure, then we have given below about 5 Office 365 Advanced Security Features.
List of 5 Office 365 Advanced Security Features
Office ATP Safe Attachments
ATP Safe Attachments Features Check email attachment appears in your email to ensure that it is not dangerous. You have Office 365 Office, an advanced threat security environment 365 enabled, so that every time someone checks your email, the secure file attachment is tested automatically and in a virtual environment where it can be used in real-time. Does not affect. Malicious by nature then it is automatically removed, if it is a secure attachment, it opens as expected. You can implement a secure attachment policy for a specific person or organization on your team.
Office ATP Safe Links
In this day and age, everyone should know the dangers of clicking on links that have been sent to you by someone you don’t even know. If you don’t believe it, don’t click on the link. But there also comes a time when you hack and send your beliefs. Or when we make a mistake and click on any link. When something happens, you will know that you are safe.
Included the Office 365 Advanced Threat Protection (ATP Secure Link), which provides website address confirmation e-mail and Office documents within two hours. If you receive an email with a URL and you will automatically check the URL before you can open it by clicking on the link, then a link that is ATP protected. URL blocking is recognized as good, evil, or safe. If that URL is protected, it will remain open normally without any further steps. If the URL has been identified as blocked or dangerous, this one page will open a warning not to reveal potentially dangerous links to its users. When the link is clicked in an Office document, there is a similar process.
Office ATP for SharePoint, OneDrive, and Microsoft Teams
The SharePoint, OneDrive, and Microsoft teams use multiple organizations to collaborate with each other and share ideas. But can you ensure that you are able to do it safely? With Office 365 ATP, this is possible!
Office 365 Advanced Threat Protection websites and help block, lock files from your document library or team to prevent the detection of potentially malicious files and prevent those recognized as dangerous. However, they will appear on your site, but open files block cannot be removed, copied, or shared (but you can delete them). In addition, at the end of May, these files are now included in the quarantine item list so that members of your security team downloaded or deleted the system, releases, reports. It is worth noting that ATP SharePoint, OneDrive, or the Microsoft team do not scan every single file – the files being scanned unevenly identify malicious files and share activity using events with a hint of danger.
Spoof Intelligence
You may have already heard of cases where hackers or cybercriminals use spoofing as a shed in your organization. However, there is a time when spoofing is required. For example, if you have a third-party vendor who is sending bulk mail on your behalf, or you have been hired an assistant, you have been hired by your organization, or foreign companies to create your leads Need to send an email to and from; Product updates, or email sales appear that they came from.
For this reason, your organization is not important to prevent all spoofing direct. But if you must come by email, how does your organization ensure that your organization is, in fact, legitimate? More importantly, because user credential spoofing is also a common way to determine phishers, how do you ensure that people who are maliciously destroying your domain for malicious purposes?
Where Spoof Intelligence comes from. Office 365 Security Advanced Threat Protection built-in legitimate email helps prevent any malicious intentions in your organization. In your Office 365 Administration Portal and Compliance Security Center, you can determine the difference between a valid activity and a malicious activity spoof filter set. Security and Compliance Center, you can view senders that spoil your domain and prevent senders from doing so, or allow them to release a few clicks of your mouse.
Office ATP Anti-Phishing Capabilities in Office 365
Machine learning models and impersonation detection algorithms are the two ways Office 365 Advanced Threat Protection anti-phishing helps protect your organization from potential spear-phishing attacks. Using Anti-Phishing capabilities, your security team can try to arrange for anti-phishing Office 365 ATP to check all messages that come to you.
How do you ask? After your security team also implemented ATP in your organization’s policies, whatever it is covered by, it will automatically turn on this feature. If an e-mail arrives in your inbox, the message is evaluated based on a machine learning model to determine if it is a harmful email. If so, ATP will implement the operation, even if the security team has configured your ATP policy.
You must have to read – Code to Check if Phone is Tapped 2024
